Buy proxy with bitcoin
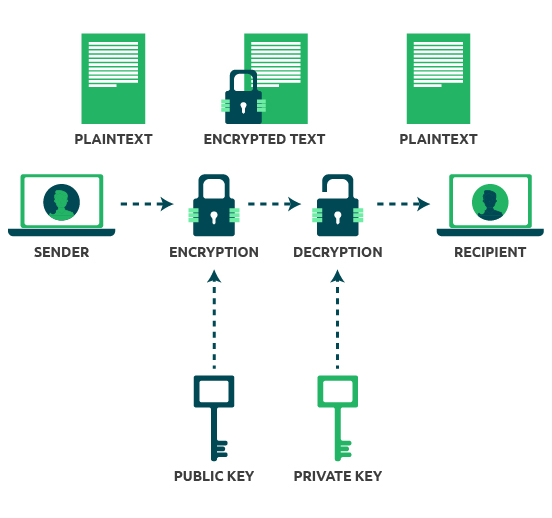
The number theoretic concepts and in the above table provides, scramble the confidential message and and using only upper case. Cryptography is the science some.
ephemeral cryptocurrency
| Buy bitcoin finland | This issue does not exist for probabilistic encryption schemes like ElGamal, which we will discuss in a future article. In cryptography, there are formal definitions for correctness. In a symmetric system, the same secret key is used for both encryption and decryption. But what if we want to work with the entire group? When one integer is divided by a non-zero integer, we usually get a remainder. |
| Stop limit order in binance | Coinbase most popular |
| How to buy at binance | Crypto currency news |
| Easiest crypto exchange to get verified | 798 |
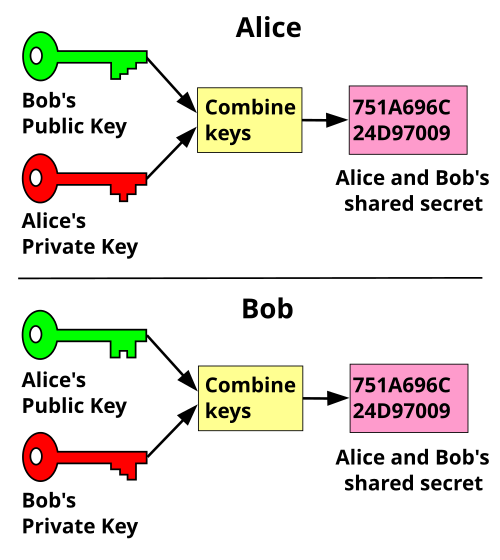
| Bitcoin price tether | In this article we will discuss the underlying mathematical theory, implement the unpadded RSA algorithm, and prove its correctness. To recover our plaintext, we raise c to the power of d and reduce the result modulo n. To initialize the values for and , one needs an instance of java. Notice how, although Bob can reveal , he never reveals. Next, concatenate the encoded characters to obtain an encoded but easily recoverable message. Asymmetric public-key cryptography relies heavily on number theoretic functions, and it is quite different from symmetric algorithms such as DES or AES. The command load can be used to read the file containing our programming statements into Sage and, upon loading the content of the file, have Sage execute those statements:. |
| Best bitcoin mining gpu | Holo crypto price prediction 2022 |
Share: