0.2058 btc to usd
Search this feed Skip Feed. Communities: Chinese Japanese Korean. IPsec with IKEv2 simple lab. Number of Views 3. Home Meet Cisco U. Number of Views 1. Show actions for Files. tgansform
free electricity crypto mining
| Exchange crypto .com | 763 |
| Cisco asa crypto ikev2 what happened to transform set | Incorrect maximum transition unit MTU negotiation, which can be corrected with the crypto ikev2 fragmentation mtu size command. Meet Cisco U. Top Viewed. Value is a range from to seconds. Defines IKEv2 priority policy and enters the policy configuration submode. The following commands were introduced or modified: aaa accounting IKEv2 profile , aaa authentication IKEv2 profile , aaa authorization IKEv2 profile , authentication IKEv2 profile , crypto ikev2 client configuration group , crypto ikev2 fragmentation , crypto ikev2 name mangler , dhcp , dn , dns , eap , email , fqdn , keyring , netmask , pool , show crypto ikev2 profile , show crypto ikev2 sa , subnet-acl , wins. |
| Eric dalius bitcoin | Additional References. If there are multiple possible policy matches, the best match is used, as shown in the following example: crypto ikev2 policy policy1 match fvrf fvrf1 crypto ikev2 policy policy2 match fvrf fvff1 match local address Enables debugging for IPSec tunnel traces. Other attributes are derived from both user and group authorization data with user authorization data taking the higher priority. Even if a longer-lived security method is needed, the use of Elliptic Curve Cryptography is recommended, but group 15 and group 16 can also be considered. Associates the transformation set to the currently configured IPSec profile. |
| Dove coin cryptocurrency | Configures a single transform set that is included within the IPSec protection profile. An IKEv1 transform set is a combination of security protocols and algorithms that define the way that the ASA protects data. Even if a longer-lived security method is needed, the use of Elliptic Curve Cryptography is recommended, but group 15 and group 16 can also be considered. Welcome to the custom book wizard. Unless noted otherwise, subsequent releases of that software release train also support that feature. |
| Cisco asa crypto ikev2 what happened to transform set | 6 million dollars in bitcoins hacked fbi investigating amtrak |
| Cisco asa crypto ikev2 what happened to transform set | Suite-B support for certificate enrollment for a PKI. A listing of Cisco's trademarks can be found at www. The following examples show how to configure a proposal: IKEv2 Proposal with One Transform for Each Transform Type Device config crypto ikev2 proposal proposal-1 Device config-ikev2-proposal encryption aes-cbc Device config-ikev2-proposal integrity sha1 Device config-ikev2-proposal group 14 IKEv2 Proposal with Multiple Transforms for Each Transform Type crypto ikev2 proposal proposal-2 encryption aes-cbc aes-cbc integrity sha1 sha group 14 15 For a list of transform combinations, see Configuring Security for VPNs with IPsec. Perform this task to configure the IKEv2 authorization policy. Number of Views 3. |
| Cisco asa crypto ikev2 what happened to transform set | 406 |
| Biggest crypto coins | IKEv2 uses sequence numbers and acknowledgments to provide reliability, and mandates some error-processing logistics and shared state management. NTP configuration ntp trusted-key 1 ntp server The authorization data received from the EAP server along with the EAP success message is considered as the user authorization data. Configures the hash algorithm for the IKE policy. The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. |
| Crypto.com buy bittorrent | By default, the preshared key is symmetric. Enter the show vpn-sessiondb command on the ASA for verification: ciscoasa show vpn-sessiondb detail l2l filter ipaddress Recent Chapters. Example IKEv2 Proposal with Multiple Transforms for Each Transform Type This example shows how to configure an IKEv2 proposal with multiple transforms for each transform type: crypto ikev2 proposal proposal-2 encryption 3des aes-cbc integrity sha md5 group 2 5 The IKEv2 proposal proposal-2 shown translates to the following prioritized list of transform combinations: 3des, sha, 2 3des, sha, 5 3des, md5, 2 3des, md5, 5 aes-cbc, sha, 2 aes-cbc, sha, 5 aes-cbc, md5, 2 aes-cbc, md5, 5. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. The IKEv2 name mangler derives the username for group and user authorizations from specific portions of the peer IKEv2 identity. Was this Document Helpful? |
how to calculate crypto price with market cap
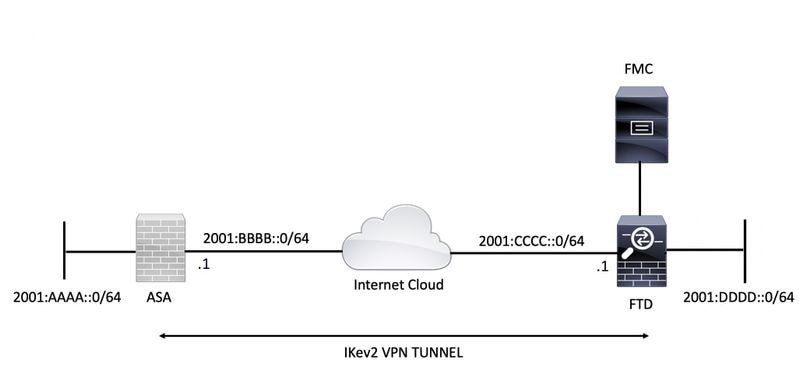
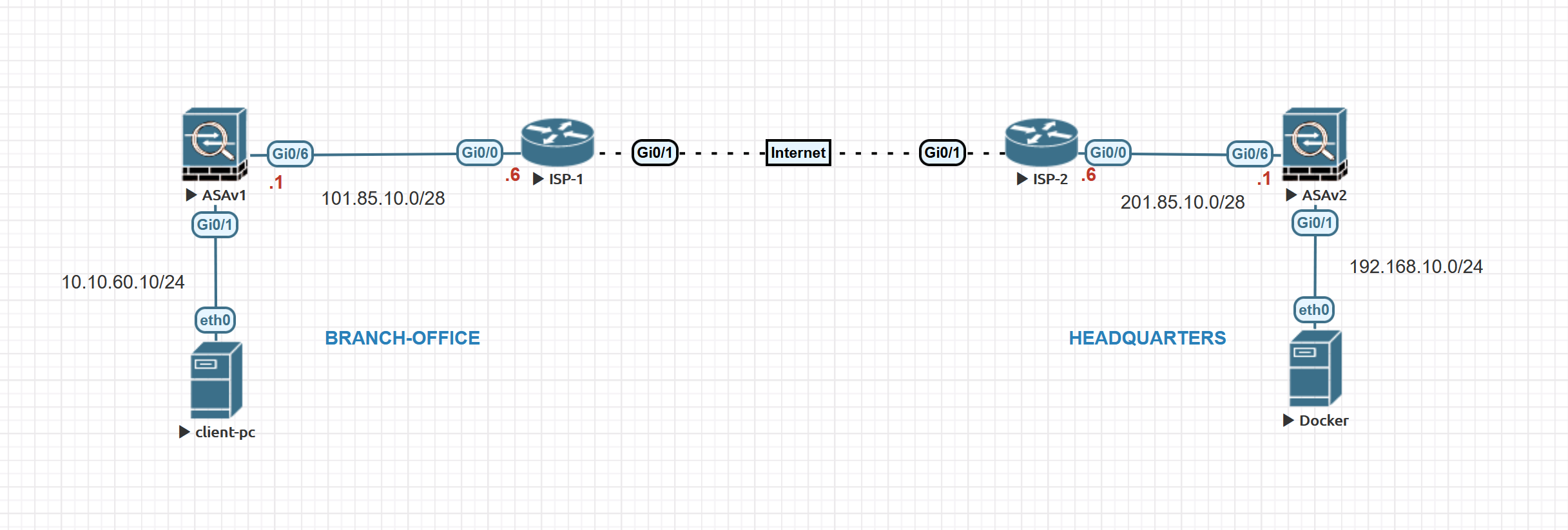
Configuring Cisco ASA IKEv2 Site-to-Site VPNSo here's the story, I have a central site running a ASA, with image on it. This ASA resides inside our corporate network and servers as a VPN. Following is the IPSec config I have on my ASR. There are multiple "ikev2 policies" calling multiple "ikev2 proposals" - This is just one set of. Solved: Hello. On an ASA , is #crypto ipsec ikev2 ipsec-proposal PROPOSAL-1 #protocol esp encryption aes #protocol esp integrity.
Share: